Cyber Security Risk Management
Cyber Security Risk Management Framework
- Research and formulate the company's overall cyber security-related management measures and rules.
- Construction, inspection, evaluation and recording of cyber security equipment.
- Check the security of personal information equipment from time to time.
- Regularly check information security control points.
- Approval, promotion and review of cyber security policies.
- Distribution of responsibilities among members of the cyber security management team.
- Develop cyber risk assessments and regular or irregular cyber security-related tests.
- Implement cyber security-related education, training and publicity from time to time.
- Maintenance and audit of company confidential information.
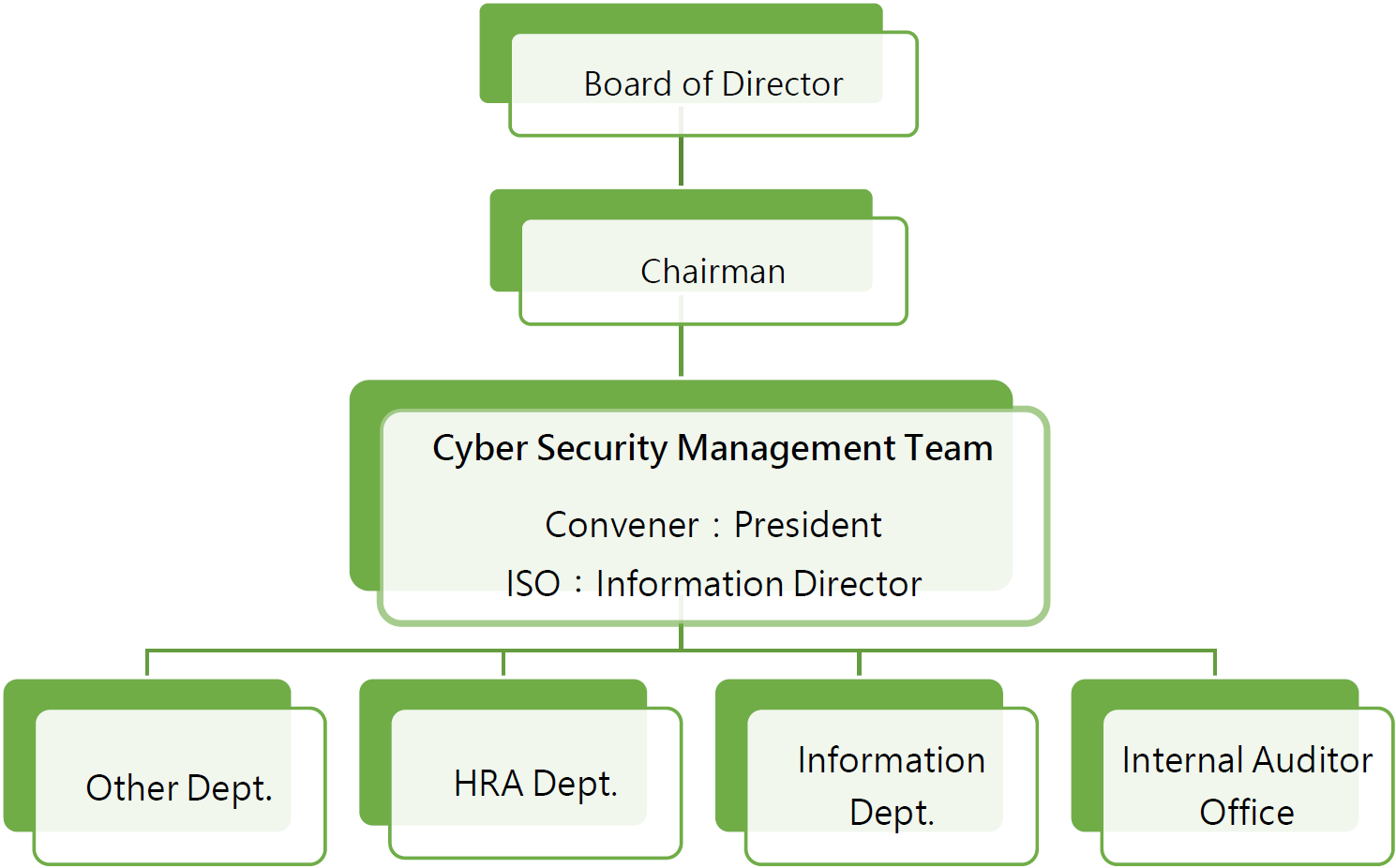
Organizational Chart
Cyber Security Policy:
- In order to maintain the company's sustainable operation and development, strengthen information processing security at each location, maintain the safe maintenance of the company's overall data, system architecture, equipment, and networks, and achieve the following goals:
- All information and systems within the company must be accessed with authorization to ensure their confidentiality.
- All information and systems within the company are protected from unauthorized modification to ensure their accuracy and completeness.
- Establish a backup plan for all information and systems within the company to ensure availability.
- Formulate cyber security operating procedures, including core business and its importance, cyber system inventory and risk assessment, cyber system development and maintenance security, cyber security protection and control measures, cyber system or cyber service committee external management measures, cyber security incident notification response and intelligence assessment response, continuous improvement of cyber security and performance management mechanism, etc.
- All personnel who use information systems should take cyber security promotion courses, and supervisors and personnel responsible for information security should take cyber security professional course training from time to time.
Cyber Security Policy Objectives:
- Implement cyber security management to ensure sustainable operations
- Actively prevent and detect risks and effectively control risks.
- Continuous cyber security training to improve service quality
Invest Resources in Cyber Security Policy Management:
In order to strengthen the cyber security management within the company, ensure the confidentiality, integrity and availability of all important information within the company, and comply with the relevant control operations of the "Principles for Establishing Internal Control Systems for Public Offering Companies". The "Cyber Security Management Team" is established, with the President as the Convener, the Information Department as the dedicated information security unit, and the Information Director as the Information Security Officer. It is responsible for the coordination and promotion of cyber security management matters. Its team members include the Information Department, the Human Resources Administration Department, and the heads of each unit. , and internal auditors, etc. are responsible for promoting, coordinating and supervising the following matters, and reporting the implementation status to the board of directors at least once a year:
Implement the cyber security system, implement it by all employees, and continuously monitor, review and audit various information systems to ensure their confidentiality, integrity and availability. Regularly conduct cyber security risk assessments, identify possible cyber security risks for core business and core information systems, analyze the impact of loss of confidentiality, integrity and availability, and implement corresponding cyber security management or technical controls measures etc. Protect information assets from risks such as leakage, damage or loss due to external threats or improper management by internal personnel, build a safe network environment, and ensure the goal of sustainable operations.
In addition to daily equipment maintenance, we also provide system vulnerability detection services and Web security detection services at any time. The equipment policy planning is adjusted based on the emergency response process, and reviews are conducted regularly and quarterly based on the analysis of information security incidents to ensure that when information systems fail or major disaster events occur, control can be quickly blocked to ensure the continued operation of key businesses and will The risk of loss is minimized.
All personnel who use information systems should take cyber security awareness courses. In addition, supervisors and personnel responsible for information security should take information security professional course training from time to time to enhance colleagues' cyber security awareness and intelligence, strengthen their adaptability, and improve service quality.
Implement the cyber security system, implement it by all employees, and continuously monitor, review and audit various information systems to ensure their confidentiality, integrity and availability. Regularly conduct cyber security risk assessments, identify possible cyber security risks for core business and core information systems, analyze the impact of loss of confidentiality, integrity and availability, and implement corresponding cyber security management or technical controls measures etc. Protect information assets from risks such as leakage, damage or loss due to external threats or improper management by internal personnel, build a safe network environment, and ensure the goal of sustainable operations.
In addition to daily equipment maintenance, we also provide system vulnerability detection services and Web security detection services at any time. The equipment policy planning is adjusted based on the emergency response process, and reviews are conducted regularly and quarterly based on the analysis of information security incidents to ensure that when information systems fail or major disaster events occur, control can be quickly blocked to ensure the continued operation of key businesses and will The risk of loss is minimized.
All personnel who use information systems should take cyber security awareness courses. In addition, supervisors and personnel responsible for information security should take information security professional course training from time to time to enhance colleagues' cyber security awareness and intelligence, strengthen their adaptability, and improve service quality.
Report information to the board of directors in 2023
Report information to the board of directors in 2023